I just wanted to make note of some r1 jailbreak details. David Buchanan: Jailbreaking RabbitOS (The Hard Way) carroot: rabbitOS tethered jailbreak
Author: v3ritas
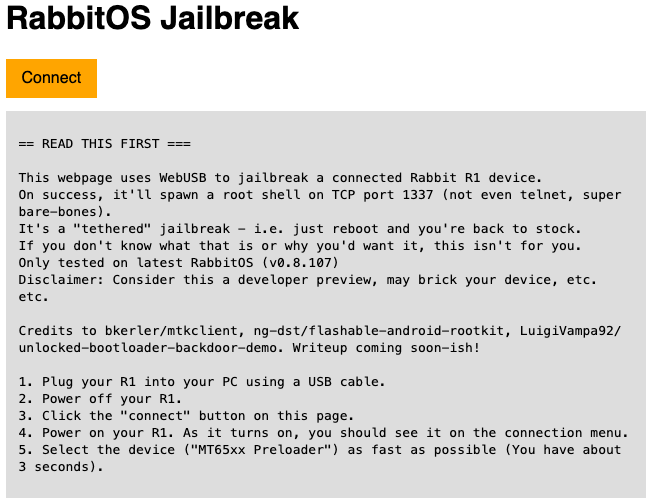
Rabbit r1 Jailbreak
I haven’t tried it yet, but just saw someone mention an r1 jailbreak that doesn’t modify any partitions so shouldn’t affect OTA updates. It’s also tethered, meaning if or when the device reboots, it’s back to stock (which isn’t necessarily a bad thing). In case anyone was interested: RabbitOS Jailbreak
Instructions to get stock Android or LineageOS21 on the Rabbit r1 (July 2024)
A few people have been running into issues while trying to get stock Android or LineageOS on their Rabbit r1’s, so I was trying to flesh out some of the documentation: GitHub Gist: veritas06 / Rabbit_r1-Android_Guide.md. Instead of doing GitHub Gists, I’m thinking it will be a lot easier if we have a Wiki that […]
RabbitOS 20240615.10/0.8.103(134D8EC)
New OS update for the Rabbit r1 yesterday, & I used mtkclient to dump the partitions. Hoping to be able to get Magisk working at some point… haven’t had much luck with it recently.
Android Authority: “Rabbit R1, a thing that should just be an app, actually is just an Android app (Updated)”
Ouch… so it looks like Rabbit isn’t have a good day. And right around when the devices are getting delivered (which probably isn’t a coincidence). See, it turns out that the Rabbit R1 seems to run Android under the hood and the entire interface users interact with is powered by a single Android app. A […]
Upgrading LineageOS + Magisk
Making a note for myself because I spent like an hour trying to figure this out… I’m running LineageOS 21 (Android 14) & just had an OS upgrade. Problem was that I rebooted when the process was done instead of having Magisk flash to the inactive slot, meaning I’m not rooted when my tablet starts […]
More WordPress Issues =]
Apparently I’m still having issues with some themes in WordPress just failing to get the site to load… I should probably just see about getting a backup of everything, wiping, & starting clean in case it’s just residual settings from previous themes & upgrades. We’ll see how that goes.
WordPress Issues…
This seems to be a recurring theme… no pun intended. I was trying to edit or switch my theme from Libre because I had just a blank column down the side that I finally wanted to address. That led to trying multiple different themes, before finally settling on this one, at least for now…
The M1: A Compact Multitool for Technophiles & Hackers
A friend mentioned this to me & of course I had to back the device, since it looks like a Flipper alternative, but has Wi-Fi built into their board. I’ll admit, I do still need to read all of their details, but if the community here is anything like Flipper’s, & for only $119 on […]
![v3 Cube [PNG]](https://v3ritas.tech/wp-content/uploads/2018/06/v3-Cube-1.png)